2. Unlocking keys¶
The Next button on the main window allows reading keys and checking if they are valid. On successful key unlock the application will proceed to the operations screen.
2.1. Software keys¶
Software keys are the easiest to start with and are supported by all OpenPGP implementations.
2.1.1. GnuPG¶
GnuPG can list all secret keys that are already in your keyring with gpg -K:
$ gpg -K
-------------------------------
sec ed25519 2023-07-21 [C] [expires: 2026-07-17]
B67B41795629C36DE6E6672ED548E8C0100BF1A5
uid [ unknown] testing cert
The secret key can then be exported to a file using the following command:
$ gpg --export-secret-keys --output key.pgp B67B41795629C36DE6E6672ED548E8C0100BF1A5
key.pgp file can then be directly used in Private Key Store
Server. Select it using the first button and, if the file is password
protected provide it in a second textbox. Pressing Unlock will check
if the key is valid and usable. If the file is corrupted or the
password provided is wrong the application displays an error.
2.1.2. New key¶
If you do not have a software key one can be generated using gpg --gen-key or, alternatively using sq command line tool:
sq key generate --userid 'Test <test@example.com>' --export key.pgp
2.2. Smartcard keys¶
Private Key Store Server additionally supports smartcards using OpenPGP Card protocol. This includes Nitrokeys, Yubikeys or any other token exposing OpenPGP Card applet.
The application will scan available cards on startup and add them to the list. After typing in User PIN (PW1) and clicking Unlock the key details will be printed in the second part of the window.
Provisioning the card is outside of the scope of this project but we
recommend using opgpcard tool, which uses the same native
Rust communication with the smartcard.
2.3. Common problems¶
2.3.1. Unlocking certificate¶
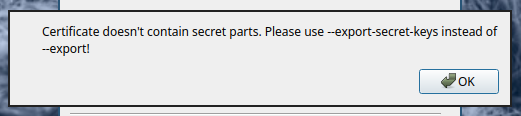
If the certificate doesn’t contain secret keys (e.g. it was exported
from GnuPG using --export option instead of --export-secret-keys)
the appropriate error message is displayed:
2.3.2. Secret key not encrypted¶
The secret key may be protected by a password. That exact password is required to unlock it. If the secret key is not protected by a password then no password need to be provided. Otherwise a “secret key not encrypted” error will be displayed.
2.3.3. Bad password¶
If the certificate cannot be read, e.g. it is encrypted but the password provided does not match an “unexpected EOF” error is displayed.
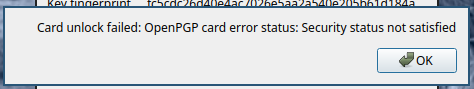
2.3.4. Bad PIN¶
If the PIN provided to the OpenPGP Card does not match a “security status not satisfied” error is displayed: