5. Web Operations¶
The Private Key Server can also expose a web server so that authorized sites can execute cryptographic operations right in their UI without leaving the browser.
By default two sites are authorized:
https://arm.services.metacode.biz/tencrypt/
http://localhost:8076 (for testing and development)
5.1. Enable remote requests¶
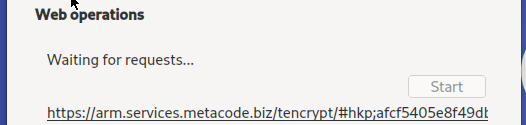
Private Key Server requires explicit user action for enabling web operations. After clicking “Start” the local HTTP server will be started. Only connections from authorized sites that are listed will be processed.
After the server is started the window will display “Waiting for requests…” message:
5.2. tencrypt¶
Tencrypt is a small OpenPGP operations site spun out of Keyoxide. The webapp originally supported only public key operations (that is verification and encryption) but as part of this project it was extended to support private key operations (signing and decryption).
By default the site requires an key to start with. Try this sample key.
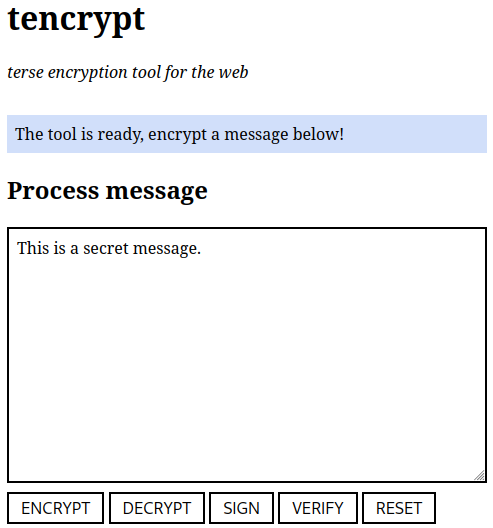
5.2.1. Encrypt¶
Encrypt is a public key operation and as such, doesn’t require the Private Key Server to be running. The key to be encrypted to will be the key used to open tencrypt:
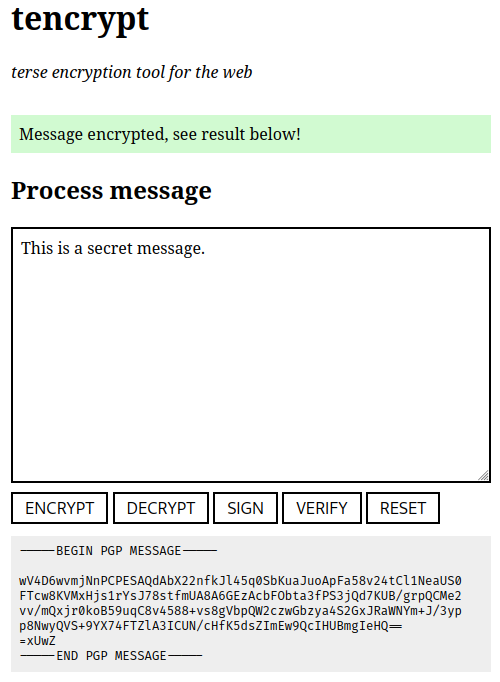
After encryption the application will print an ASCII-armored block of OpenPGP data:
5.2.2. Decrypt¶
The decryption is a private key operation and needs a Private Key Server to be running. It accepts an ASCII-armored block of encrypted data:
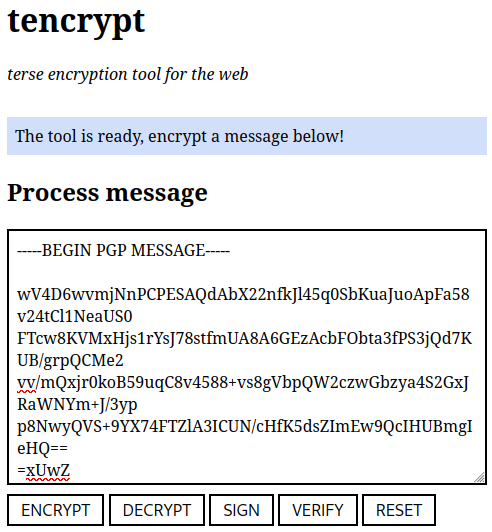
After successful decryption the cleartext will be printed below:
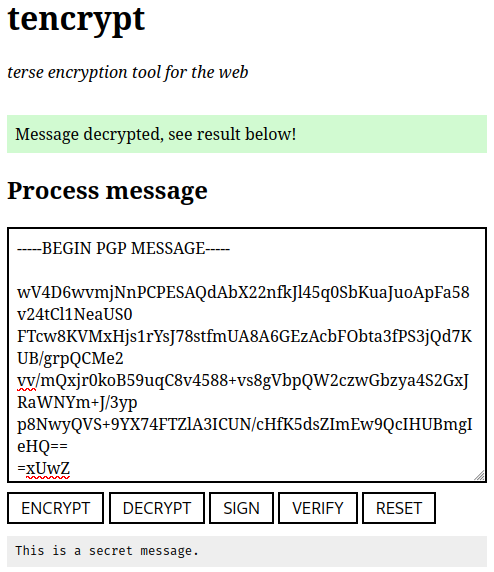
5.2.3. Sign¶
Data signing is a private key operation and needs a Private Key Server to be running. It accepts plain text that will be signed:
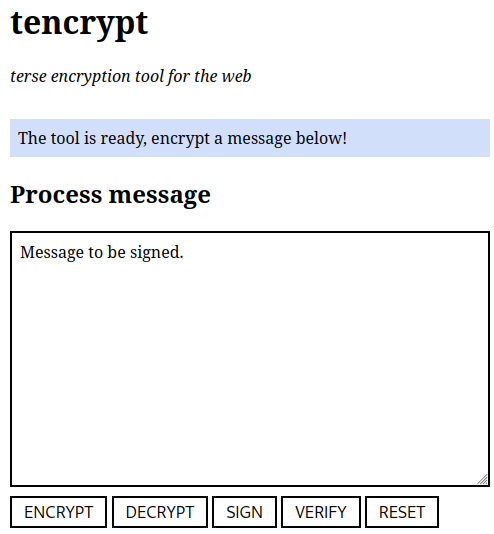
After signing the application will print an ASCII-armored block of OpenPGP data, which contains both the signed data, as well as a signature:
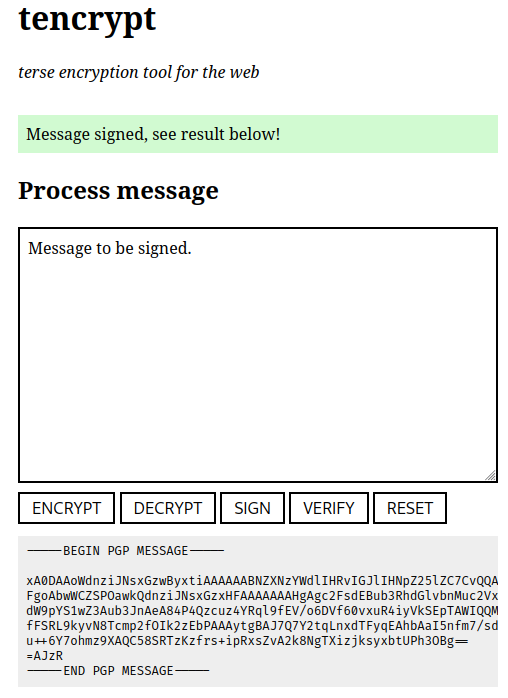
5.2.4. Verify¶
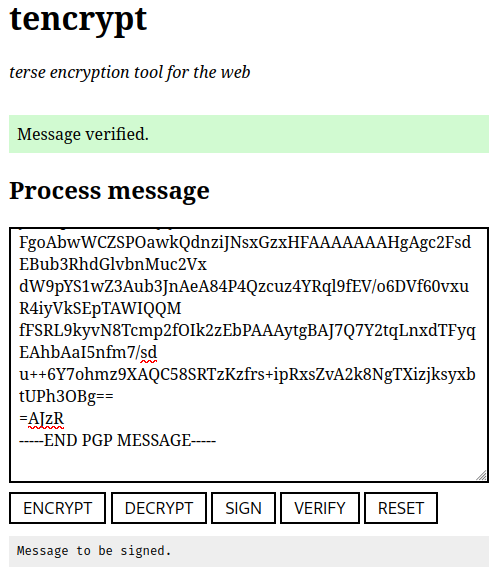
Verification checks if the signature made by the key is valid and accepts an OpenPGP ASCII-armored message which contains signed text and a signature:
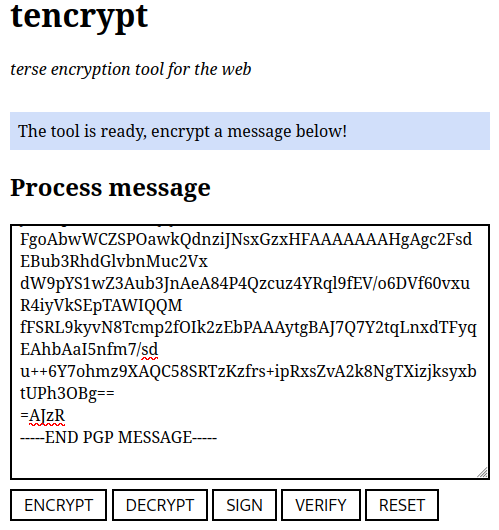
If the signature is valid the application prints the data which was signed: